The deployment of 5G networks across Asia and globally has introduced unprecedented security challenges that require comprehensive cybersecurity strategies to protect critical infrastructure, customer data, and operational integrity. As telecommunications networks become increasingly software-defined and virtualized, the traditional security perimeters dissolve, creating expanded attack surfaces that sophisticated threat actors are eager to exploit. With Asia accounting for 34% of global cyber incidents as of 2024 and experiencing an average of 2,510 weekly cyberattacks per organization—marking a 23% increase from the previous year—the imperative for robust 5G cybersecurity has never been more critical.
The 5G Security Landscape
5G networks introduce fundamental architectural changes that create new security challenges while potentially addressing some limitations of previous generation networks. The shift toward software-defined networks, network function virtualization, and cloud-based infrastructure expands the potential attack surface while requiring new security approaches and technologies.
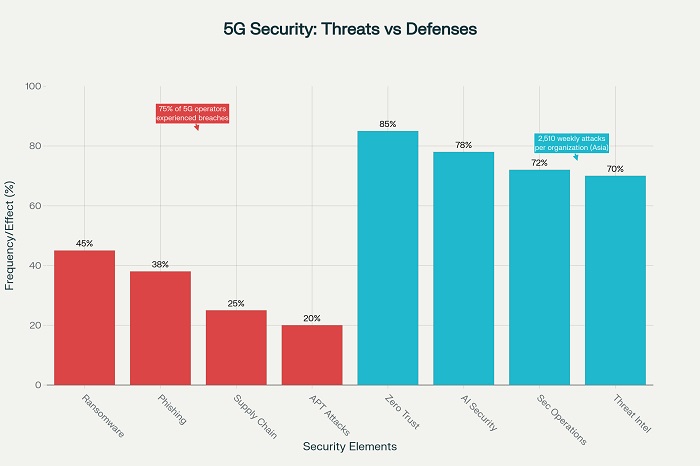
Despite initial expectations that 5G would enhance network security through improved protocols and architecture, practical implementation reveals significant challenges. Nokia’s research indicates that nearly three-quarters of 5G network operators experienced up to six security breaches or cyberattacks in the past year, demonstrating that “breaches are the rule, not the exception” in the current environment.
Regional Threat Landscape
Asia-Pacific Vulnerability
The Asia-Pacific region faces particularly acute cybersecurity challenges due to its rapid digitalization and growing role as a digital economy powerhouse. In 2024, the region experienced significant growth in cyber incidents, with countries including Singapore, India, China, South Korea, and Southeast Asian nations seeing increased attack frequency and sophistication.
This surge in cyber incidents reflects the expanded attack surface created by accelerated digital adoption ranging from e-commerce to IoT implementations. The growth has positioned Asia as accounting for 34% of global cyber incidents, underscoring the urgency of collective defense strategies and enhanced cybersecurity preparedness.
Emerging Threat Vectors
Advanced Persistent Threats represent sophisticated and persistent cybersecurity challenges that target telecommunications infrastructure for espionage or disruption. Nation-state actors and organized cybercriminals deploy these advanced techniques that require proactive and sophisticated threat detection and response strategies.
Supply chain risks pose significant challenges as telecommunications companies rely on global supply chains for hardware and software components. Compromised equipment can introduce vulnerabilities that are difficult to detect and mitigate, requiring comprehensive supplier security assessment and management programs.
Technology-Specific Security Challenges
Network Function Virtualization Risks
The virtualization of network functions creates new security considerations as traditional hardware-based security controls become less effective. Software-defined networks require different security approaches that address virtual environments while maintaining performance and operational efficiency.
Network slicing capabilities in 5G create isolated virtual networks that require individual security management while ensuring isolation integrity. This complexity multiplies security requirements while creating new opportunities for targeted attacks against specific network slices or customer segments.
Cloud Integration Security
5G networks’ increasing reliance on cloud infrastructure introduces cloud-specific security challenges including data protection, access control, and service availability. The integration of cloud and telecommunications security requirements creates complex compliance and operational challenges.
Multi-cloud and hybrid cloud deployments common in 5G infrastructure require sophisticated security orchestration across different platforms and service providers. This complexity demands enhanced security expertise and advanced security management tools.
Critical Infrastructure Protection
Core Network Security
5G core networks handle vast amounts of sensitive data while supporting critical applications that require guaranteed security and availability. Data privacy and protection become increasingly important as networks handle more personal and commercial information while complying with strict regulations including GDPR and CCPA.
The centralized nature of 5G core functions creates high-value targets for cybercriminals while requiring comprehensive protection strategies. Security failures in core network components can affect entire service areas and multiple customer segments simultaneously.
Edge Computing Security
Edge computing deployment in 5G networks creates distributed security challenges as computing resources move closer to end users. Each edge location requires individual security management while maintaining consistent security policies and procedures across the entire network.
The proliferation of edge computing nodes multiplies potential attack vectors while requiring local security capabilities that may lack the sophisticated protection available in centralized data centers. This distributed security challenge requires new approaches and technologies for effective protection.
Industry Response and Solutions
Zero Trust Architecture
Zero Trust security models operate on the principle of “never trust, always verify,” providing enhanced security for 5G networks by continuously validating every device and user attempting to access network resources. This approach significantly reduces unauthorized access risks while providing granular control over network access and resource utilization.
Implementation of Zero Trust architectures requires comprehensive identity management, device verification, and network access control capabilities. These systems provide enhanced security while enabling flexible access policies that support diverse 5G use cases and applications.
Artificial Intelligence for Security
AI and machine learning technologies provide powerful tools for 5G network security through real-time threat detection, anomaly identification, and automated response capabilities. These technologies can analyze vast amounts of network data to identify potential threats and respond quickly to security incidents.
Machine learning algorithms can identify patterns and behaviors that indicate potential security threats while reducing false positive rates that plague traditional security systems. This capability enables more effective security operations while reducing the operational burden on security teams.
Regional Security Initiatives
Government and Regulatory Response
Malaysia’s establishment of a National 5G Cybersecurity Testing Centre demonstrates proactive government response to 5G security challenges. The facility will facilitate vulnerability assessments, compliance validation, and security protocol testing for industry stakeholders.
The partnership between Digital Nasional Berhad and CyberSecurity Malaysia aims to establish comprehensive 5G security guidelines that serve as benchmarks for future security protocols. This collaboration includes threat intelligence sharing and enhanced cybersecurity capabilities to counter emerging threats.
Industry Collaboration
Singapore’s regulatory approach includes strict security and resilience requirements for 5G network design and deployment. The Cybersecurity Act amendments in May 2024 expand coverage beyond critical information infrastructure to regulate cybersecurity of foundation digital infrastructure including data centers and cloud service providers.
The GSMA’s telco security landscape research provides comprehensive analysis of cybersecurity challenges and strategies across the Asia-Pacific region. This industry collaboration facilitates knowledge sharing and best practice development to enhance regional cybersecurity capabilities.
Operational Security Strategies
Security Operations Centers
Real-time threat detection and response capabilities become essential for 5G network security through Security Operations Centers that monitor network activity and respond to security incidents. These facilities require advanced technologies and skilled personnel to effectively identify and respond to sophisticated threats.
Automation plays a critical role in security operations as manual processes cannot scale to address the volume and complexity of modern cybersecurity threats. Nearly two-thirds of network operators report that security staff spend more than 30% of their time on manual security tasks that could be automated.
Threat Intelligence and Analytics
Advanced threat intelligence capabilities enable telecommunications operators to identify emerging threats while sharing information with industry partners and government agencies. This collaborative approach enhances collective defense capabilities while improving individual operator security posture.
Analytics platforms process vast amounts of security data to identify patterns and trends that indicate potential threats. These capabilities support proactive security management while enabling more effective resource allocation for security operations.
Future Security Evolution
6G Security Preparation
The development of 6G networks requires security considerations from initial design phases to ensure comprehensive protection against evolving threats. Cyber resilience in the age of 6G must address the expanded capabilities and increased complexity of next-generation networks.
Security-by-design principles become essential for 6G development as retrofitting security into deployed networks proves insufficient for addressing sophisticated threats. This approach requires collaboration between network developers, security experts, and regulatory authorities.
Quantum Security Implications
Quantum computing development poses long-term security challenges for telecommunications networks while also providing potential security enhancements through quantum encryption technologies. Operators must prepare for both the threats and opportunities presented by quantum technology advancement.
The timeline for practical quantum computing deployment creates urgency for quantum-resistant cryptography development and implementation. This transition requires careful planning and coordination to maintain security while enabling technology evolution.
The strengthening of cybersecurity in the 5G era represents a critical imperative for telecommunications operators, governments, and the broader digital ecosystem. Success requires comprehensive strategies that address technical, operational, and collaborative dimensions of cybersecurity while maintaining network performance and service quality. Organizations that invest effectively in 5G cybersecurity position themselves advantageously for long-term success while contributing to overall digital ecosystem security and resilience.
The evolution of cybersecurity threats and defensive capabilities will continue as 5G deployment expands and 6G development progresses. Continuous adaptation, investment, and collaboration become essential for maintaining effective protection against increasingly sophisticated threats while supporting the digital transformation that 5G networks enable.